Ransomware have been part of the IT landscape for a long time now, however, it has become more prominent in the last two years with an ever increasing number of attacks that get more and more clever over the iterations. In this blog we will see how Nakivo Backup and Replication can help you mitigate the risk of data loss in case of Ransowmare attack.
We already talked about vSphere environments in the Ransomware landscape in a previous blog and what VMware is doing about it.
Before getting stuck in, note that you can get an unrestricted 15-days free trial of Nakivo Backup and Replication. Check out this blog for guidance on how to get started with it.
Air-Gapped Backups
First off, implementing a solid backup infrastructure is paramount to ensure that you have access to backups in case of recovery post ransomware. However, ensuring that the backup infrastructure is secured and isolated from the rest of the network is even more important as it will be no use if your backups have been hit as well.
This is what is called air-gapped backups. It can be achieved through network isolation or by using the backups to tape feature of NAKIVO Backup and replication.
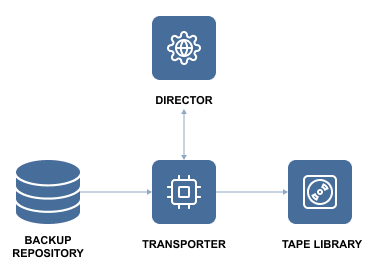
On top of this, you can schedule when the repository is attached to create an “air gap” between the attacker and your backups.
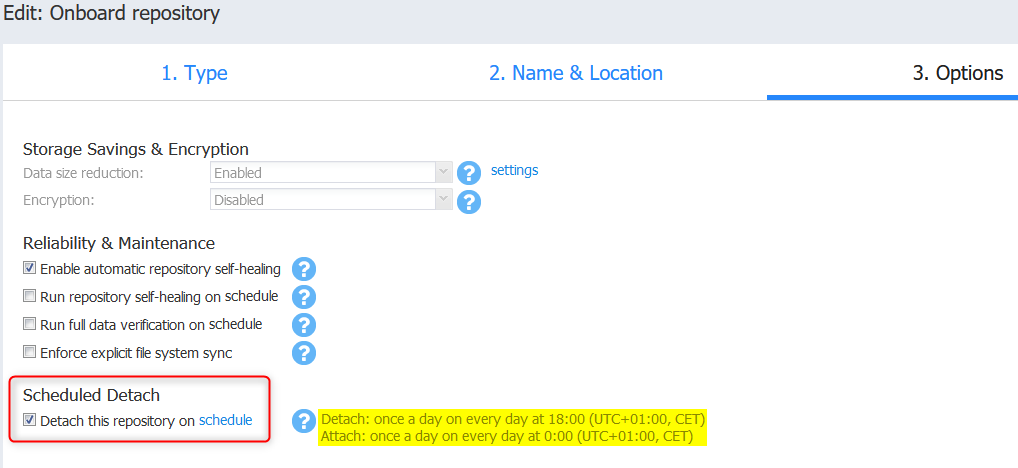
Immutable repository
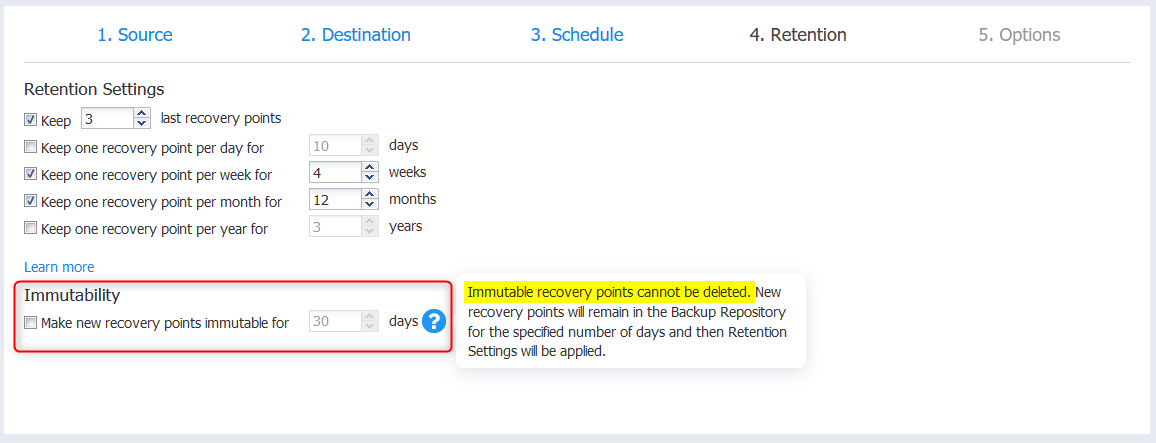
The other area to look out for is Backup Immutability. NAKIVO Backup & Replication allows you to make the recovery points in repositories immutable for local folders and S3 storage.
When immutability is enabled, the recovery points are stored using the write-once-read-many (WORM) model. The result is that you make recovery points immutable for x days. The recovery points remain immutable for the specified number of days, effectively protecting them from ransomware attack targeting backup systems.
Hardened Virtual Appliance
NAKIVO Backup & Replication v10.5 (currently in beta as of October 2021) offers the Hardened Virtual Appliance (VA). A simple way to deploy NAKIVO Backup & Replication and protect data against ransomware.
You can simply deploy the NAKIVO Backup & Replication as a pre-configured virtual appliance powered by Ubuntu Server and protect your data from deletion and encryption by ransomware. Backups sent to a repository deployed as part of the VA can be made immutable for a specified period of time.
Two-Factor authentication (2FA)
Many Ransomware attacks related by organizations that got hit involved compromised credentials, be it Active Directory or local authentication. By enabling two-factor you essentially add an extra layer of security to your backups.
With 2FA enabled, users need a code provided by the Google Authenticator mobile app or by email to access the solution and backups. Paired with the role-based access control (RBAC) feature in NAKIVO Backup & Replication, you also make that no one is able to perform unauthorized operation
Best practices implementation
This one is true not only for NAKIVO Backup & Replication but for every single backup solution out there. Ensuring that you are following Backup best practices doesn’t mean you will never get owned, however it will make it significantly harder for bad actors which will most likely move on to easier targets.

- Create Regular Backups: You don’t want to find yourself left with a 2 months old copy of your data when it is time to restore from backup. NAKIVO Backup & Replication lets you set aggressive RPO and RTO to ensure minimal data loss and downtime.
- Follow the 3-2-1-1 Rule: You probably heard of the 3-2-1 rule, keep 3 copies of data on 2 different media types, 1 copy offsite. Well now you need to add 1 last line of defense; an immutable copy on S3, local Linux-based repository or on tape.
- Create an Effective Retention Policy: Regular backups are great but you also need to tune your retention policies. You can save up to 4,000 recovery points for each backup job with NAKIVO Backup & Replication and rotate them with the grandfather-father-son (GFS) retention scheme.
- Set Up Automated Workflows: With the Policy-Based Data Protection feature, NAKIVO Backup & Replication lets you create rules to automatically protect your VMs and EC2 instances which match certain criteria. That way no VM is left on the side of the road.
- Control Access to Backup Data (2FA): I shall reiterate here the importance of 2FA to connect to NAKIVO Backup & Replication with the role-based access control (RBAC) feature and the principle of least privilege (PoLP).
- Verify Recoverability of Your Backups and Replicas: Test your backups and replicas regularly and verify that they are valid with the instant verification capability of NAKIVO Backup & Replication and be alerted if something went wrong. That way you won’t discover it when it’s time to restore the VM.
There are obviously a whole lot more actions you can take to further harden your backup infrastructure by implementing secured Active Directory, network segmentation, Email and browser hygiene, antivirus software, least privelege access policy…
Wrap up
Ransomware have been creeping around and ramping up in the last few years but they are not going anywhere anytime soon. For that reason it is recommended to educate your IT department and the users (arguably even more so) to the risks of cyber attacks. Most large ransomware attacks start with something silly like a phishing email that could be quickly debunked if the user knew what to look out for.
Regardless, user education isn’ the only vector of attacks so protecting your infrastructure at all the layers is paramount. And if, root forbid, you got your data encrypted by ransomware, your last line of defense would be your backups. In which case, the features from NAKIVO Backup & Replication we described above would help you ensure your backups don’t get encrypted as well.